|
Since June 2013 every Member has a SOCKS5 proxy included in his Account by default and is free to use, if desired. To explain what a SOCKS 5 proxy is and what it is good for, below gives a brief overview first.
nVPN offers on each of its countries and for every member by default a SOCKS 5 Proxy solution, which can be used as a standalone proxy, OR additionally in combination with OpenVPN.
In order to gain extra safety, you can as well start chaining now: "other VPN service using OpenVPN => nVPN SOCKS5"
Aimed for maximum Anonymity, the setup includes all the typical approaches like "/dev/null 1>&2" and running under an unprivileged user, makes the SOCKS5 solution logless (and as well acceptably secure)
Some Users - even when using TCP/443 - are still facing restrictions, or still being unable to browse with OpenVPN reliably, in such cases the SOCKS5 proxy for straight browsing, simple downloading activities, can be a real good alternative!
What is SOCKS proxy server and what is HTTP proxy server?
Actually SOCKS and HTTP proxy severs, both behave in the same way. They are forwarding your requests to the destination host (address). With help of SOCKS or HTTP proxy servers, you could bypass any firewall restriction and access any web site like: facebook.com, myspace.com, bebo.com, youtube.com
So what is the actual difference between HTTP proxy server and SOCKS proxy server?
HTTP proxy server - the HTTP proxy server was originally designed to be used only with HTTP protocol. To say it simpler, if you need to open any http:// or https:// like web address, HTTP (SQUID) proxy servers are the best solution in 90% of cases. There are almost no difference between SOCKS and HTTP proxy servers, if they are used for HTTP protocol (we will speak about rare cases bit later).
SOCKS proxy servers - the SOCKS proxy servers are more flexible and do not seize you. While HTTP proxy servers could hide your IP only when you are browsing a web page, SOCKS5 proxy server can keep your information private, even when you are using such programs like ICQ, Skype, MSN or even email clients like Outlook, TheBat, Thhunderbird.
SOCKS proxy servers are designed to be used with ANY protocol you wish.
Can HTTP proxy server used in the same way like SOCKS proxy server?
It is said here Bust the myth: SOCKS better than HTTP proxy that if you will use CONNECT method of HTTP proxy server, then HTTP proxy server could be used for any protocol, the same like SOCKS proxy server. That definition is right, but with one exception: in 90% cases HTTP proxy server limits protocols for which CONNECT method could be used. Basically CONNECT method is allowed only for HTTP protocol over SSL or https:// like web addresses. That is because HTTP proxy server filter/updates client's each request. They need to change header information before they will forward it to the destination host, meanwhile SOCKS proxy servers work more like an open relay. SOCKS proxy server tunnels data directly to the destination host (address) as it comes from the client, without changing anything in the source.
That is why SOCKS servers are so useful and cannot be replaced with simple HTTP proxy servers.
What are the differences between SOCKS4 and SOCKS5?
The number 4 and 5 refers to the version of SOCKS protocol. These two versions are the most popular and became wide spread all over the world. The following new features were implemented in 5th version: various authentication mechanisms, support of UDP protocol and IPv6.
We do not think that you will ever use directly UDP protocol, but there is a high chance that the program, for which you need to use proxy server, will use it. In that case nor HTTP neither SOCKS4 will work, the only solution to keep your IP hidden would be to use SOCKS5.
Another advantage of SOCKS5 are the many various authentication mechanisms. Without authentication, the SOCKS proxy server is publicly available, even if you do not want it to be a public one. As soon as you will setup SOCKS4 proxy server, any person can use it without permission, he/she just needs to know IP and the port of SOCKS proxy server.
What are the advantages of SOCKS proxy server?
SOCKS proxy servers work as open relay. That means there are no limitations for which protocols SOCKS proxy server will be used. Such no limitations allow it to use a SOCKS proxy server for creating ‘proxy chains’. If you ever heard the term ‘proxy chain’ then SOCKS is that type of proxy servers, which are used to create those . Here is the principle how it works, one proxy establishes connection to another, that proxy in turn establishes connection to the next one and so on... so you could have several proxy servers chained:
As example: You » OpenVPN » SOCKS1 » SOCKS2 » SOCKS3 » SOCKS4 » Destination host
As more SOCKS proxy servers are involved in a proxy chain, the higher is the security and privacy level.
Also SOCKS proxy servers can create reverse connections. In some cases your local administrator could block all outgoing connections for security reasons. At the same time incoming connections could be kept open. In that case instead of establishing connection from your PC to SOCKS proxy server, you can ask SOCKS proxy server to establish connection with your PC. After that, communication between client and SOCKS proxy server will remain the same as if use establishes connection by his/her own.
Some good further reading sources found on google:
http://en.wikipedia.org/wiki/SOCKS
http://www.secpoint.com/What-is-SOCKS5.html
http://etherealmind.com/fast-introduction-to-socks-proxy/
Benefits of SOCKS5:
[+] Fast(er) speed (but no Encrypted Traffic!!)
[+] For a simple IP change with specific Applications only
[+] You decide which Applications (Skype, uTorrent, Email, FTP and so on..) should be getting a new IP (in the contrary to OpenVPN, where the ENTIRE Traffic is routing through the VPN)
[+] Good for just downloading from OCH (One Click Hosters like Rapidshare and so on, meanwhile our SQUID proxy could be the better solution for this)
[+] Good for restricted Environments like China, Offices, School, Firewalls (Places where even a TCP/443 Method doesnt work)
Downsides of SOCKS5:
[-] No Traffic Encryption (atleast not by default: read further down to the bottom and learn how to Encrypt the traffic with SSL)
[-] Not all Applications support SOCKS5 Proxy with User authentification (Browsers like Firefox, Chrome, IE D NOT support the SOCKS5 proxy by default as it lacks an User Authorization possibility)
[-] Additional software can be required to install to route the traffic either completely, or partially through SOCKS5, some really nice solutions are ProxyCap ($30.00 after 30 days trial) or Proxifier ($39.95 after 31-days trial )
[-] IP is only changing where the SOCKS5 proxy is set
The login details are always the same, regardless how you connect:
Hostname: uXXXXX.nvpn.to (the uXXXXX.nvpn.to hostname you can find in your .ovpn config file)
Port: 9999
Username: Your VPN username
Password: Your VPN password
How to use it with ProxyCap:
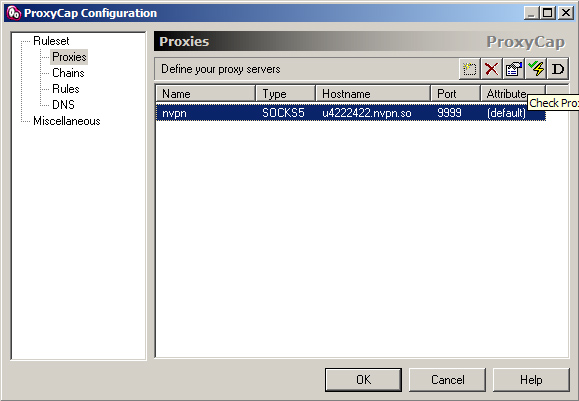
1. Proxies -> New Proxy Server
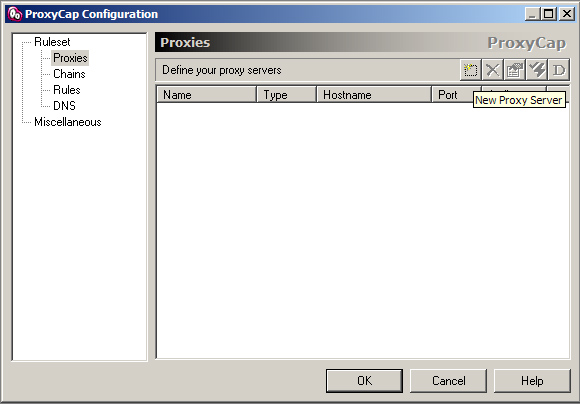
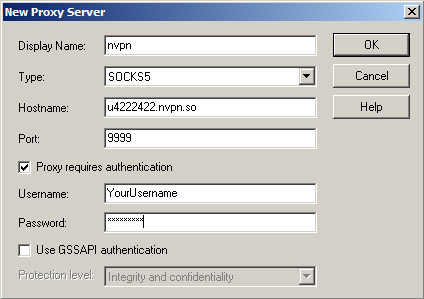
2. Enter your details as below, your "uXXXXX.nvpn.to" hostname you can find in your .ovpn config file. (Username/Password same as for the VPN)
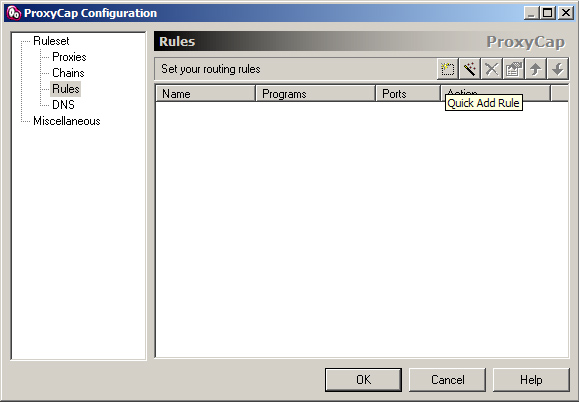
3. Go to Rules -> Quick Add Rule
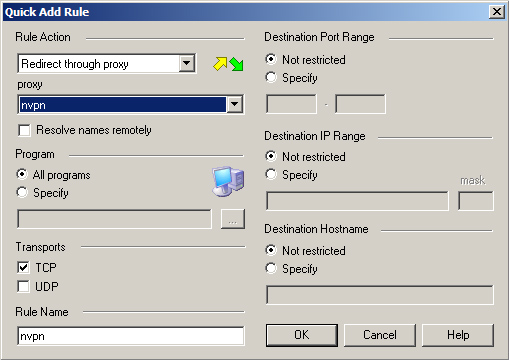
4.Choose details like shown (alternatively you can here choose to only route specific programs through the proxy)
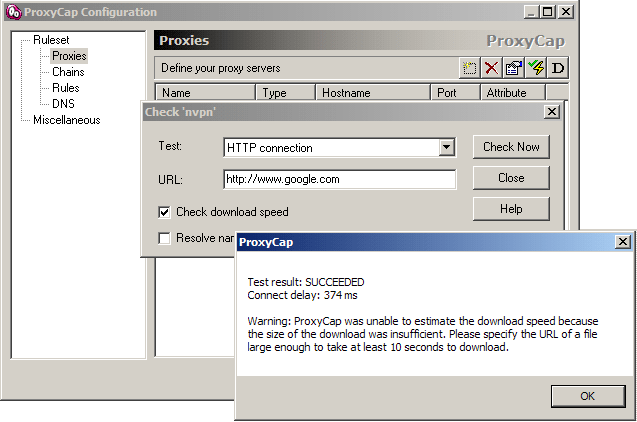
5. Proxies -> Check Proxy Server (a simple proxy connectivity test before you enable it)
6. Test shows success, we can proceed enabling the Proxy now!
7. Enable ProxyCAP (Enable the Proxy in the Taskbar icon now)
8. Your chosen traffic will now be going through the SOCKS5 Proxy. Test the IP change on a IP test website like: www.whoer.net
Update 01.12.2013: Since from today on you have the possibility to as well ENCRYPT your SOCKS5 traffic!! How? Follow the steps described below to get it accomplished:
1. You need the open source program "stunnel" Choose your version and download it.
2. We need to do some changes now in the stunnel config file, start stunnel and right click its icon located in the taskbar, click on "Edit Configuration" and place following into the file (dont matter where):
client = yes
[nvpn-socks]
accept = 127.0.0.1:1080
connect = uXXXXX.nvpn.to:9998
(Your hostname you find in the openVPN config file it starts with uXXXXX.nvpn.to)
*2.1* Incase you dont want to edit the file manually yourself, or have troubles doing it, simply click on this link to generate it on the fly: https://nvpn.net/memberss/stunnel.php?generate=true
After clicking the link (its possible you need to log in first) inside the members area you will find a new Download link for your "stunnel.conf" file! (This generated config file is ready to go for both proxies, Squid + Socks5)
3. IMPORTANT: After editing the file it needs to be reloaded, right click again on the stunnel icon and click on "Reload stunnel.conf"
4. To verify your data flow you can activate the "Show Log window" now.
5. Start your prefered tunnel software now, in our given example here we will stick to "proxycap" and there you go to "Configuration" -> "Proxies" and we edit it:
Type: SOCKS5
Hostname: 127.0.0.1
Port: 1080
Username: Your VPN username
Password: Your VPN password
6. As last step go to "Rules" -> "Ports" choose "Specifiy" and we add some ranges now:
First port: 1
Last port: 1079
First port: 1081
Last port: 9997
First port: 10000
Last port: 65535
7. Click on "Enable ProxyCap" to get the tunnel started and watch your data flow in stunnel log window, you will see similar events like below:
2013.12.01 22:32:24 LOG5[18660:16728]: Service [nvpnsocks] accepted connection from 127.0.0.1:59701
2013.12.01 22:32:24 LOG5[18660:16728]: connect_blocking: connected 91.236.116.100:9998
2013.12.01 22:32:24 LOG5[18660:16728]: Service [nvpnsocks] connected remote server from 192.168.1.197:59702
2013.12.01 22:32:25 LOG5[18660:16728]: Connection closed: 3127 byte(s) sent to SSL, 654 byte(s) sent to socket
2013.12.01 22:32:30 LOG5[18660:14496]: Service [nvpnsocks] accepted connection from 127.0.0.1:59705
2013.12.01 22:32:30 LOG5[18660:14496]: connect_blocking: connected 91.236.116.100:9998
2013.12.01 22:32:30 LOG5[18660:14496]: Service [nvpnsocks] connected remote server from 192.168.1.197:59706
2013.12.01 22:32:31 LOG5[18660:4820]: Service [nvpnsocks] accepted connection from 127.0.0.1:59709
2013.12.01 22:32:31 LOG5[18660:4820]: connect_blocking: connected 91.236.116.100:9998
2013.12.01 22:32:31 LOG5[18660:4820]: Service [nvpnsocks] connected remote server from 192.168.1.197:59710
8. Your Traffic is now encrypted with SSL. Verify the IP change on some IP-check website and thats it.
| 






